Five years ago, Apple decided to open its bug bounty program to everyone, marking a major change in how it handles security research. Previously, it had operated on an invitation-only basis and was focused solely on iOS. That expansion also came with a substantial financial incentive, raising the maximum reward from $200,000 to a headline-grabbing $1 million.
Now, the company is pushing the boundaries once again. This November, Apple will update its Security Bounty program, doubling the top potential reward to an unprecedented $2 million. This seven-figure sum is reserved for a very specific and severe type of discovery: fully weaponized exploit chains that function like the most advanced mercenary spyware. To qualify, these attacks must achieve their goals with no interaction from the user whatsoever.
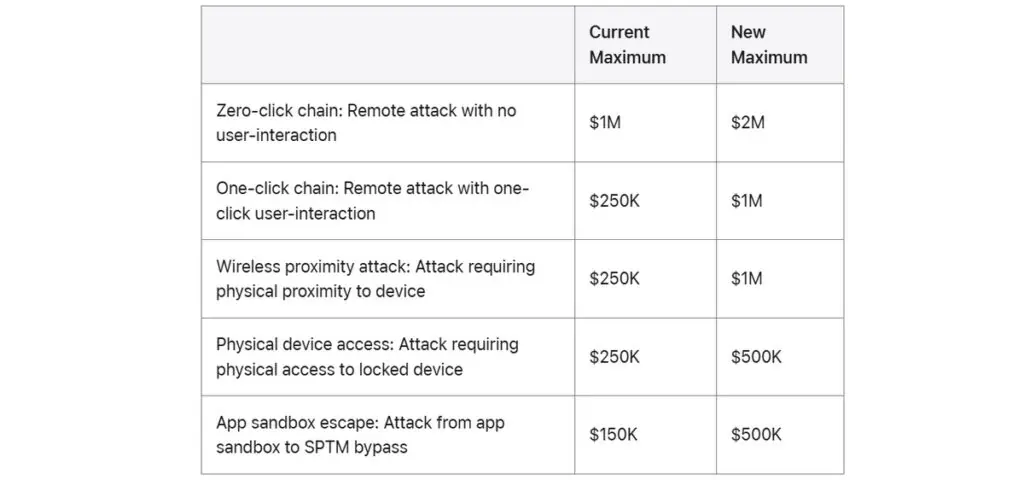
While $2 million is an extraordinary figure on its own, the total payout for a researcher could be even higher. Apple has implemented a bonus structure for finding multiple critical vulnerabilities, meaning a single researcher could potentially walk away with more than $5 million.
The increases aren’t limited to the top tier. Apple is substantially raising bounties across the board. Rewards for discovering one-click exploit chains, as well as attacks that require physical proximity to a device, have both quadrupled from $250,000 to $1 million. The top reward for attacks on a locked device with physical access has doubled to $500,000. Even demonstrating a specific technique, like chaining a WebContent code execution with a sandbox escape, now comes with a bounty of up to $300,000.
Those numbers are pretty remarkable, though they reflect the extreme difficulty of such discoveries. Ivan Krstić, Apple’s VP of security engineering and architecture, noted in an interview with Wired that the top-tier payouts are exceptionally rare. However, he confirmed the company has made multiple $500,000 payments in recent years.
Beyond the larger rewards, Apple is also streamlining the process for researchers. A new “Target Flags” feature, inspired by capture-the-flag competitions, is being built directly into its operating systems. This allows security experts to objectively demonstrate a flaw, enabling Apple to rapidly validate the issue and process the bounty even before a software fix is developed and released.
With over 2.35 billion Apple devices active worldwide, the company’s investment in security is a core part of its brand identity. These massive bounties are a direct response to a highly sophisticated threat. Apple emphasizes that the only system-level iOS attacks it has ever seen in the wild are from mercenary spyware, multi-million-dollar exploit chains, often associated with state actors, that are used to target a very select number of individuals. This program is a key part of their strategy to counter that threat.
Maybe you would like other interesting articles?

