Mobile devices are now a core part of everyday life, keeping a significant amount of personal data within reach. With that growing dependence comes a rise in cyber threats, as attackers develop more advanced malware and spying methods.
Security company iVerify reports that it has identified a new spyware platform known as ZeroDayRAT, built to take near-complete control of an infected smartphone. The firm says the tool functions on both Android and iOS, including their latest versions, and delivers surveillance capabilities usually associated with well-funded threat actors, for those willing to afford it.
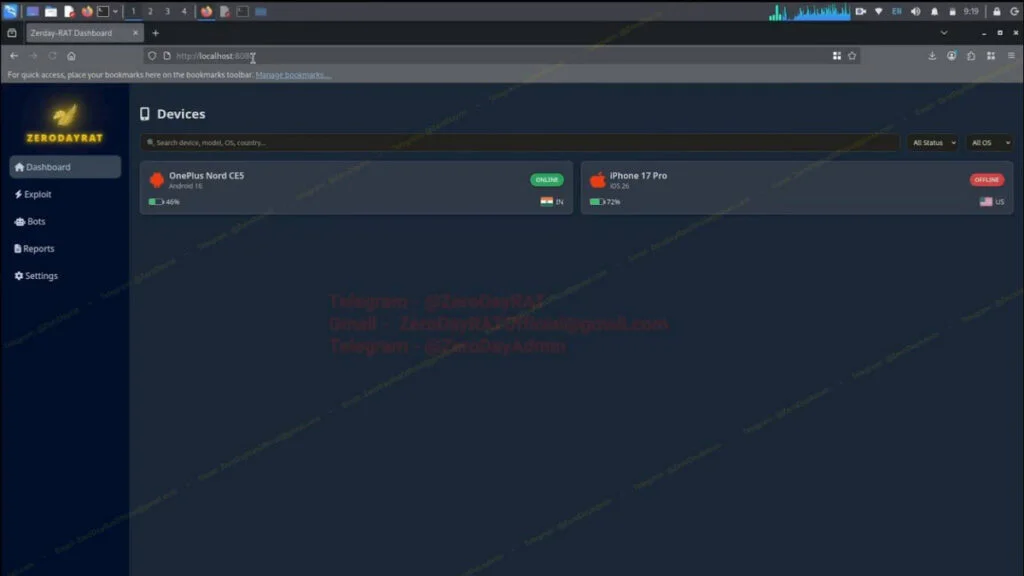
Reports indicate that ZeroDayRAT’s unnamed creator is marketing the spyware via Telegram, where it was first identified on February 2, 2026. The package is described as a commercial service that includes customer assistance, scheduled updates, and a web-based dashboard for controlling infected devices.
The security researchers describe ZeroDayRAT as a level of spyware complexity that once required nation-state backing to achieve.
Distribution primarily occurs through SMS-based phishing, commonly known as smishing. Users are directed to download an application that mimics legitimate software, which, once installed, initiates its embedded surveillance payload.
iVerify says the same payload can also be delivered through phishing emails, fake third-party app stores, and links shared via platforms like WhatsApp or Telegram.
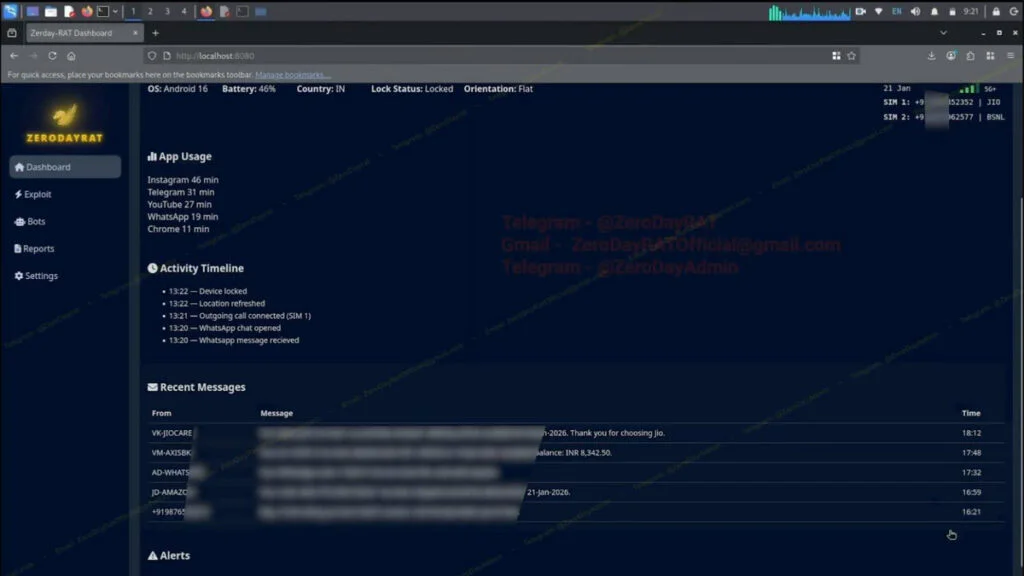
Once a device is compromised, attackers gain access to a dashboard organized into multiple tabs, each unlocking deeper levels of surveillance. The Overview tab provides high-level details about the device, including its model, operating system, battery status, country, SIM and carrier information, app usage, and more.
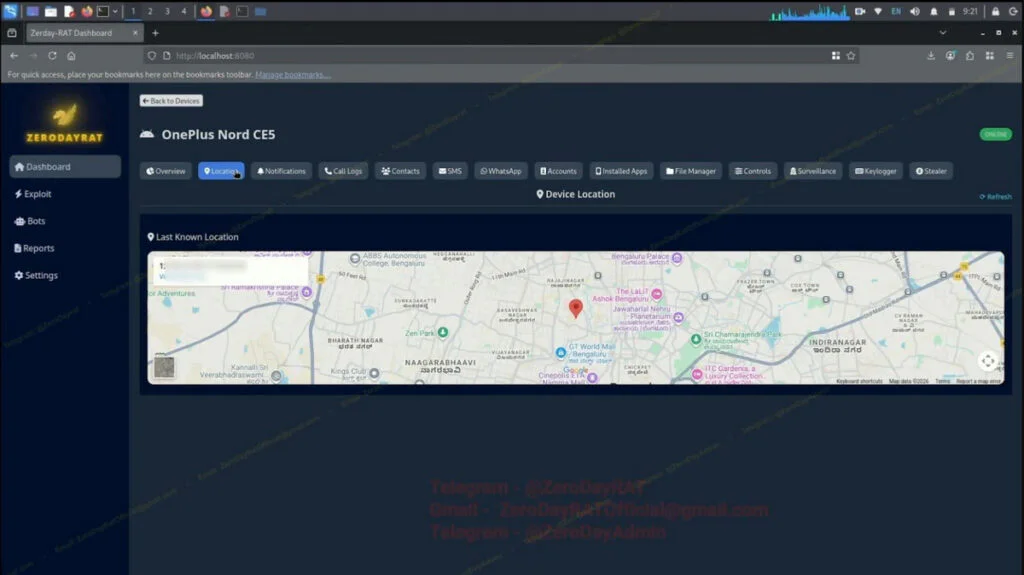
Other sections expose far more sensitive data. Attackers can view messages from banks, mobile carriers, and personal contacts. A Location tab uses GPS data to track a victim’s movements worldwide. Because the malware can intercept system notifications, it can also surface WhatsApp messages, YouTube alerts, system events, and virtually any other notification that appears on the device.
An Account tab aggregates usernames and email addresses tied to services such as Google, Facebook, and Amazon. The spyware also tracks SMS messages, allowing it to capture one-time passwords, SMS-based two-factor authentication codes, and similar security messages.
ZeroDayRAT’s most invasive functions include live monitoring and keylogging. According to iVerify, it can access the camera and microphone in real time, record the screen, and capture every input, along with a live snapshot of what is displayed.
The toolkit is also designed to target payment services, banking systems, and cryptocurrency wallets in an attempt to steal digital assets.
For individuals, an infection could result in a near-complete loss of personal privacy. Within organizations, a single compromised work device could become the gateway to a broader data exfiltration effort.
The firm warns that mobile security should be treated with the same seriousness as traditional endpoints (laptops, PCs) and email security, not as an afterthought.
Maybe you would like other interesting articles?