A critical vulnerability has surfaced in React, and researchers say the exploit requires minimal effort. With React underpinning significant portions of both web and private cloud stacks, the risk surface is considerable.
The vulnerability, considered unusually severe due to its simplicity and potential impact, affects React Server Components. Analysts at Wiz report that an attacker can run malicious code on a vulnerable server using only one crafted HTTP request.
React maintained by Meta and a broad open-source community has become a cornerstone of today’s web ecosystem. Estimates suggest it powers roughly 6% of all websites and appears in nearly 40% of cloud deployments. Its role in modern UI development also extends to frameworks like Next.js, which is now confirmed to be impacted by a linked vulnerability.
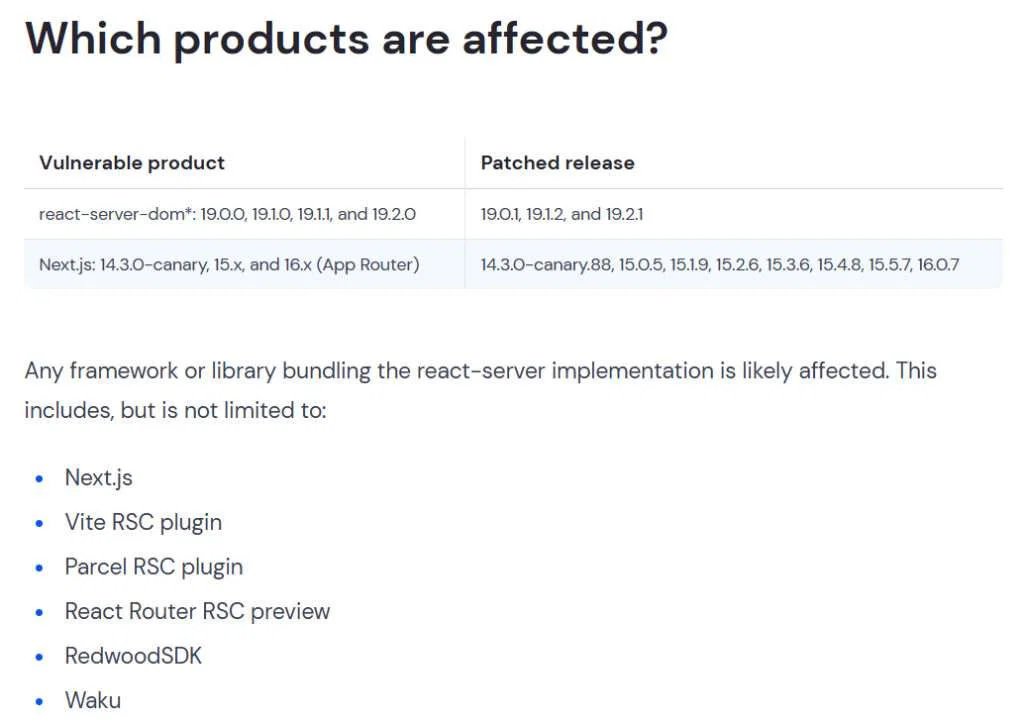
The issue, now cataloged as CVE-2025-55182 for React and CVE-2025-66478 for Next.js, traces back to an insecure deserialization step in the RSC “Flight” protocol. Researchers have named the flaw “React2Shell,” warning it allows attackers to remotely deliver and execute crafted payloads on vulnerable servers.
“The attack vector is completely remote and requires no authentication,” Wiz reported. The firm confirmed it has built a working proof-of-concept exploit, which showed near-perfect reliability during internal tests. Analysts caution that many cloud deployments run publicly exposed Next.js instances, placing them at immediate risk.
What alarms researchers most is how little effort the exploit requires. The report notes that a single crafted HTTP request sent to a vulnerable server is enough to trigger the attack, dramatically reducing the barrier for widespread abuse.
To counter the React2Shell exploit path, the React team has rolled out patched releases incorporating hardened validation and safer deserialization logic. Industry security groups are strongly recommending immediate updates across frameworks, hosting providers, and cloud environments.
“Failing to do so will make attackers’ jobs significantly easier and put users at risk,” researchers cautioned.
Although the exposure is widespread, some providers have already confirmed mitigations. Google says the default operating system images used in its Compute Engine service are not affected, but many custom deployments and independent hosting setups remain vulnerable until fixes are fully rolled out.
Organizations using React and Next.js, particularly with React Server Components enabled, are advised to prioritize updating to the latest secure versions without delay.
Maybe you would like other interesting articles?

