Google’s Find My Device, the counterpart to Apple’s Find My, has finally debuted. If you’re considering its privacy measures, it’s worth noting that Google’s version of AirTags incorporates some intelligent privacy safeguards. However, given its origin from Google, the question of trust naturally arises.
On the other hand, Apple’s Find My is renowned for its effectiveness in locating lost items. It offers undeniable convenience by allowing you to track your lost device even when it’s offline and not connected to the internet, simply by pinpointing it on a map. This feature is seamlessly integrated into Apple products like computers and AirPods, and you can expand its reach to any item by attaching or concealing an AirTag within. With Google Find My Device now available, the comparison between these two giants in the tracking realm is more relevant than ever.
Google’s assurances of user privacy are accompanied by mechanisms designed to anonymize and safeguard data. However, despite these efforts, the possibility of internal usage of location data, even in an anonymized form, remains a concern. Ultimately, trust in Google, or any tech entity, hinges on factors such as their transparency, historical practices, and the extent of privacy controls afforded to users.
In evaluating Google’s stance on privacy, it’s important to consider the company’s track record and the transparency of its practices. While they have made commitments to protect user data and employ methods for anonymization, questions persist regarding the potential internal uses of location data. Trust in any tech company is a complex calculation, and users must weigh these factors alongside the specific privacy controls available to them.
Google Find My Device (Android)
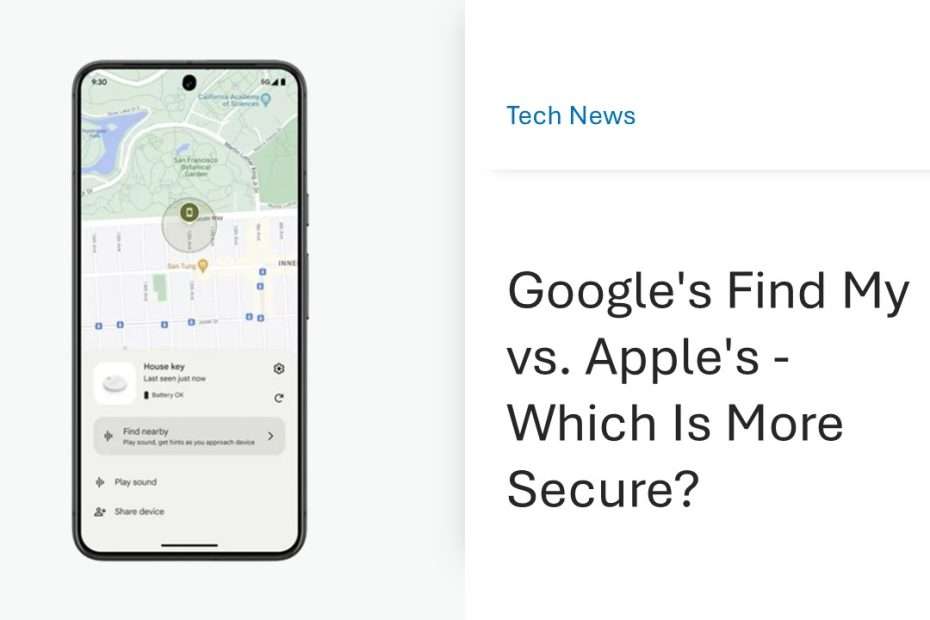
Google has recently launched its Find My Device Network, a feature that allows users to locate their Google phones using a network of third-party tracking tiles. In contrast to Apple’s approach, where they sell tracking tiles themselves, Google relies on third-party manufacturers for these devices. This means that users can purchase third-party tracking tiles that utilize Google’s network for locating their devices. Additionally, Google’s own phones, such as the Pixel 8 and 8 Pro, remain traceable even when their batteries are depleted, thanks to this network.
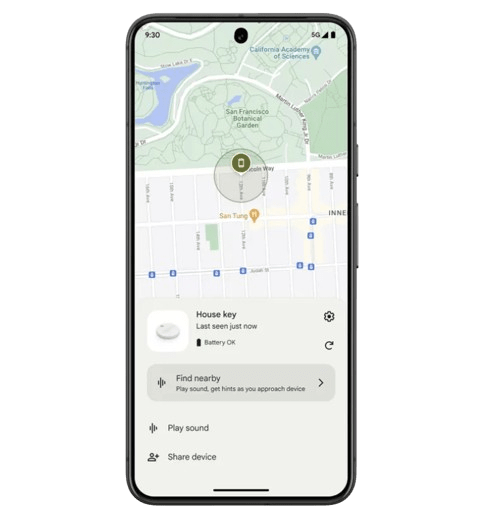
Google Find My Device functions similarly to Apple’s Find My, but it incorporates additional privacy protections. When your phone or tracking device emits periodic Bluetooth signals, these signals are detected by over a billion Android devices worldwide. The Android device receiving this signal encrypts the location and the Bluetooth ID before sending it to Google’s servers. When you use Google Find My Device, you retrieve the encrypted data packet from Google’s servers, decrypt it, and access the location information. This method allows for tracking even when the device emitting the Bluetooth signal is not connected to the internet. Certain phone models like the Pixel 8 and current iPhones are designed to reserve a small amount of battery power specifically for Bluetooth functionality, ensuring they can still be tracked even when switched off.
Google’s Find My Device network, while innovative, is not without its flaws, as demonstrated by issues with Apple’s Find My network being exploited for stalking purposes. To address potential misuse, various safeguards have been implemented to enhance user safety. For instance, unfamiliar tracking tiles emit an audible beep if they remain in close proximity to you for an extended period. Additionally, users receive alerts on their phones to notify them if a tracker is detected nearby. However, it’s important to note that if you frequently travel with someone who uses AirPods, such as a spouse or friend, their AirPods may inadvertently trigger alerts on your device, potentially leading to false positives.
Google and Apple have collaborated to create interoperability between their systems, specifically in the area of tracking alerts. This means that your Android phone is capable of detecting Apple’s AirTags, and conversely, Apple devices can detect tracking tiles associated with Google’s Find My Device network. However, Google has taken additional steps to enhance user privacy and safety, as highlighted by Dave Kleidermacher, Google’s VP of Engineering for Android security and privacy. For instance, Google’s system includes a feature where your phone will not participate in the Find My Device network when you are at home. This means that while you can still track your own devices using alternative methods like last known location or Nest finding, your phone will ignore any Bluetooth signals it detects. This strategy aims to prevent potential stalking scenarios, particularly if a stalker has planted a tracking device in your bag or car. While this approach may not be as effective in densely populated areas, it creates a protective “blank spot” around your home, especially in more remote regions.
Additionally, the Find My Device network implements measures to limit the frequency of location requests for a lost tag. Since lost items are often stationary, continuous real-time location updates are primarily useful to potential stalkers. By throttling the number of location requests, the system reduces the risk of misuse. Most notably, users have the option to opt-out of the Find My Device network entirely on their Android phones. This gives users full control over their participation in the tracking network, empowering them to prioritize their privacy and security preferences.
Despite the introduced safeguards, some individuals may still hesitate to embrace Google’s tracking technology, considering that user tracking is fundamental to Google’s advertising business model. The question arises: can Google truly separate its tracking for Find My Device from its advertising practices? While the safeguards suggest an effort to prioritize user privacy, the ultimate factor in security lies in trust. Trust is built on past behavior, and for many, Google’s extensive history in data collection raises valid concerns about the potential for misuse.
Iva Nedeleva, principal Android engineer at Private Internet Access, emphasizes the need for cautious consideration when using any technology, regardless of the developer. Trust should not be automatic, especially in the realm of data privacy. Nedeleva suggests that the most foolproof method to prevent data misuse is to ensure it never reaches the company in the first place. This sentiment reflects the reality that once data is shared with Google through its products, users have essentially consented to its use. Therefore, the decision to use Google’s tracking technology ultimately involves a balance of convenience and trust in the company’s handling of personal data.
Maybe you liked other articles too?